Is a Criminal Hacker Exploring Your Company’s Cybersecurity Defenses?
There’s a good chance that right now, a criminal hacker is exploring your small or mid-sized cybersecurity defenses for areas of weaknesses so they can launch an attack. Over four out every ten cyber-attacks target small businesses, and 60% of small businesses that are victims of a cyberattack go out of business within six months (US National Cyber Security Alliance).
The costs are staggering – lost revenues, downtime, recovery, remediation, damage to your brand and reputations … the list goes on. So staggering, in fact, that cyberattacks are projected to cause $6 trillion in damage by 2021. For small to mid-sized businesses, the average amount spent getting business back to normal after a cyberattack is over $950,000 on top of an average of $875,000 that is brazenly robbed.
The costs of doing business today must include budget for a robust cybersecurity defense and cyber liability insurance, yet less than 10% of small businesses have cyber liability insurance. Industry experts say a small business’s cyber security budget should be at least 3% of a company’s total spending (Black Stratus).
So, where should a small to mid-size business tackle the responsibility of shoring up their cyber defenses? Our recommendation: penetration testing services, beginning with a step called “Discovery”.
Brief Overview of Penetration Testing
Penetration testing is a form of ethical hacking that seeks to pierce a company’s cyber defenses to find exploitable vulnerabilities in networks, web apps, systems and user security. The key objectives of penetration testing include:
- Identify exploitable issues so that effective security controls can be implemented
- Test the robustness of an organization's security policies
- Assess a company’s regulatory compliance status
- Check the company’s employees' security awareness
- Evaluate the company’s ability to identify and respond to security issues and incidents
Penetration testing by credible experts should always be built upon frameworks and best practices from industry-recognized organizations such as the National Institute of Standards and technology (NIST), Center for Internet Security (CIS), the PCI Council, the Payment Card Industry’s Data Security Standard (PCI DSS), and the SANS Institute (officially the Escal Institute of Advanced Technologies).
Our Freed Maxick Penetration Testing methodology looks like this:
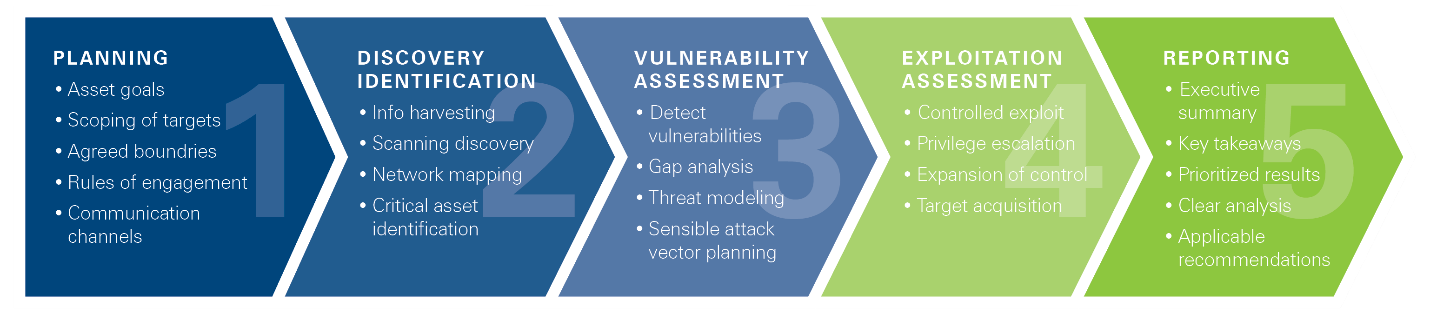
There are many different resources that go into greater detail on the costs, components, processes, and benefits of penetration testing. (For example, see Cipher.com’s “The Top 25 Reasons Why You Should Pentest”).
In today’s post, our focus is upon what we consider to be one of the early phases, and perhaps the most critical part of the penetration testing– Discovery.
Brief Overview of the Discovery Phase of Penetration Testing
In the context of cybersecurity, discovery is the practice of covertly identifying and collecting information about an organization, its networks, systems and overall external presence. Hackers will typically do reconnaissance to find points of entry for their attack, such as file permissions, running network services, OS platform, trust relationships, and user account information. This information is used to create the plan of attack for a hacker.
More than ever before, you need to put yourself in the hacker’s shoes and determine, though reconnaissance, your business’ vulnerabilities, how hackers might exploit them, and what you need to do to close or shut down those opportunities.
There are many types of reconnaissance techniques or “foot-printing” deployed in discovery, that are generally used for information gathering.
“Foot-printing” of external systems is one of the techniques that help to determine the amount of information available through public sources concerning your organization. Once gathered, an attacker will then determine the value of the information obtained through the foot-printing process that could further his/her efforts to compromise your network. The reconnaissance or foot-printing process can include, but is not limited to, the following activities:
- Online telephone directory searches
- Website(s) reviewed for information-gathering potential
- Mapping of domain names used
- Mapping of domains linked to your domain names used
- Web searches performed to discover any private or sensitive information available through public sources
- American Registry of Internet Number searches
- Domain Name Service lookups
- Traceroutes of public systems
Sources for this information cannot always be removed by an organization because the information is your company’s presence to the public. These become the stepping stone for a possible attack plan.
Additional Cybersecurity Guidance and Resources for Small and
Mid-Sized Businesses
Have questions about your company’s cybersecurity defenses, or want to discuss penetration testing services in greater depth? The Freed Maxick Cybersecurity team is happy to schedule a complementary discussion and review of your situation and current vulnerabilities.
Complete and submit our contact form today, or connect with Team Leader, Sam DeLucia, at 585-360-1405 or via email at Samuel.DeLucia@freedmaxick.com.


